Networking Architecture and Topologies
Exploring the intricacies of computer networks
Introduction:
Network architecture refers to the design of a computer network, including its physical and logical layout, communication protocols, and network components. Network architecture plays a crucial role in ensuring efficient and effective data communication, as well as determining the overall scalability, reliability, and security of a computer network.
This blog post provides an overview of computer networking architecture, discussing its components, functionality, and various types.
What is a Computer Network Architecture?
Network architecture refers to the design and structure of a computer network. It encompasses the layout, configuration, and organization of various network components and technologies that enable communication and data transfer between devices and systems. Network architecture plays a crucial role in networking by providing a blueprint for establishing efficient, reliable, and scalable networks.
The primary role of network architecture is to ensure that devices within a network can effectively communicate with each other and share resources. It defines how devices are connected, how data flows between them, and how network services are implemented. Network architecture considers factors such as network topology, protocols, hardware devices, and software components to create a coherent and functional network infrastructure.
Components of Network Architecture:
The main components of a computer network's architecture include:
Network Topology: A physical and logical layer of network components that defines how they connect and communicate with each other.
Network Media: The physical medium over which the data is transmitted, such as copper wire or fiber-optic cables.
Network Devices: Hardware components that allow communication between devices over the network, such as routers, switches and hubs.
Network Protocols: The set of rules that govern data communications between devices on a network. The most common network protocols are TCP/IP, HTTP, and DNS.
Network Security: The measures that ensure network protection, confidentiality, and data integrity.
Types of Network Architecture:
There are several types of computer network architectures, each with its own characteristics and advantages. Some of the most common types of network architectures include:
Client-Server Architecture: In a client-server network architecture, there is one centralized server that provides resources or services to multiple client devices connected to the network. The server manages network resources and handles access rights to them. The client request and receive data from the server, which acts as a central point of control. This architecture allows for centralized management, scalability, and efficient resource utilization. This type of architecture is commonly used in enterprise networks, internet infrastructure, or web applications.
Peer-to-Peer Architecture: In a peer-to-peer (P2P) network, all devices have equal status and responsibilities. There is no centralized server or administrator as in Client-Server architecture. All devices communicate directly with each other over a network without any intermediate server. Each device can act as both a client and a server, enabling the decentralized sharing of files, data and services. This type of architecture is best suited for small peer networks within a local area network, such as those used in gaming or peer-to-peer file sharing.
Hybrid Network Architecture: A hybrid network uses a combination of peer-to-peer and client-server architecture to meet the organization's specific needs. It involves a mix of centralized servers and decentralized peer-to-peer connections. This architecture offers flexibility, scalability, and the benefits of both models, allowing for efficient resource sharing and distributed computing.
Network Topology:
In network architecture, topology refers to the physical or logical arrangement of devices and connections within a network. It determines how devices are connected and data flows between them. Different network topologies have distinct characteristics that impact factors such as scalability, fault tolerance, performance and ease of management.
There are many different types of network topologies, each with its own advantages and disadvantages. Here are some of the most common types:
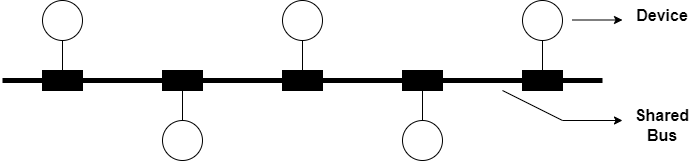
Bus topology: In a bus network, all devices are connected to a single communication channel or cable called the bus. The bus permits only one pair of devices to establish communication at a time. One end of the cable acts as the source, and the other end acts as the destination. Data travels along the bus, and each device receives the data but only processes the data intended for it. Bus topology is simple and cost-effective but can suffer from performance issues if there is heavy traffic or if the main bus fails.
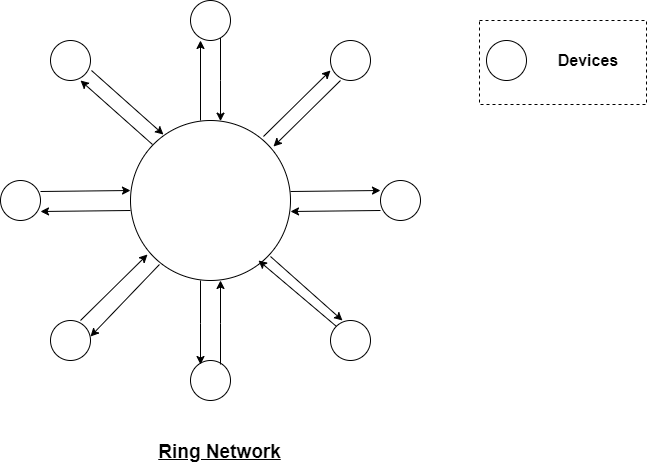
Ring topology: In a ring network, all devices are connected to each other in the form of a closed loop, where each device is connected to its adjacent devices. Ring topology provides equal access to the network resources and offers high performance. A single communication channel is often implemented to provide connectivity. Data from sending device circulates around the ring until it reaches the destination. A ring can be unidirectional or bi-directional. In an unidirectional ring, data moves in one direction only. In a bi-directional ring, data moves in both directions, but in one direction at a time. However, the failure of a single device or link in the ring can disrupt the entire network.
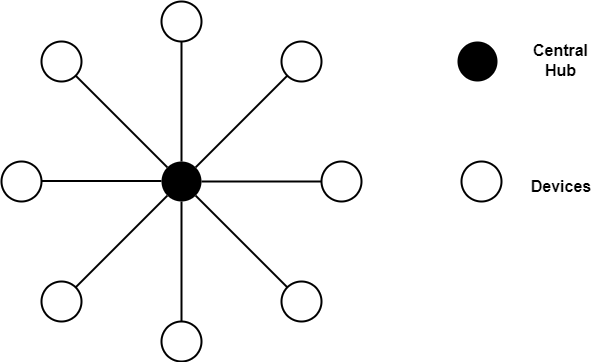
Star topology: In a star network, each device on the network is connected to the central device called a switch or a hub. Each device has its own dedicated connection to the hub, and data flows through the hub to reach the intended recipient. The hub acts as a central point of communication for all devices on the network. If one device malfunctions, it will not affect the rest of the devices on the network but if the hub malfunctions, the entire network will be affected.
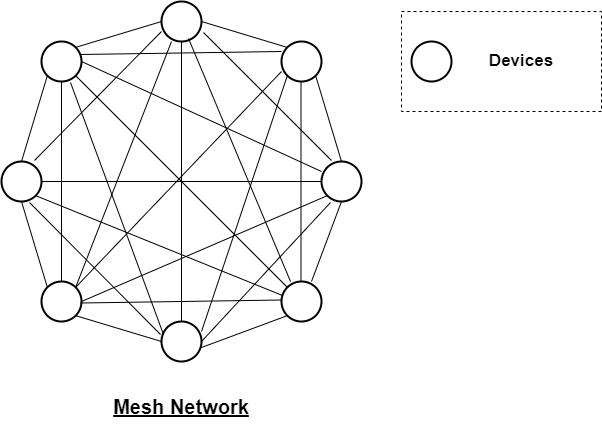
Mesh topology: In a mesh network, all devices are connected to each other in a point-to-point fashion. In a full mesh topology, every device is connected to every other device on the network. A partial mesh topology has fewer redundant connections than a full mesh. They are useful in situations, where one device frequently sends messages to all other devices. Mesh topology provides high redundancy and fault tolerance, but it can be costly to implement.
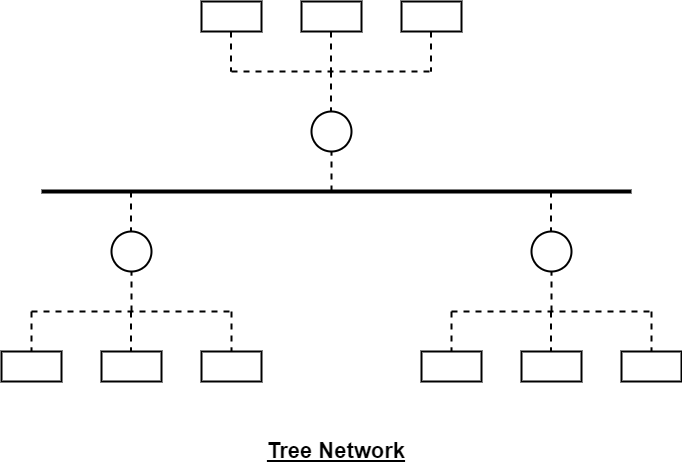
Tree topology: A tree topology, also known as hierarchical topology, is a combination of bus and star topologies. Devices are connected to a central point in a star topology, and then the central devices are connected to each other in a bus topology. The tree topology provides high redundancy and scalability, but it is complex to implement. Tree topology is commonly used in large-scale networks, such as enterprise networks or internet service provider (ISP) networks.
Conclusion:
Network architecture is a crucial factor to consider to create a highly efficient, stable, and secure network. Choosing the right network architecture depends on the organization's specific requirements and the number of devices connected to the network. A well-designed network architecture will ensure smooth data transmission, reliability, and security, leading to increased productivity, lower costs, and higher customer satisfaction.
Lastly, I would love to hear your thoughts and feedback on this article. Let us know in the comments below how you have implemented network architecture best practices in your own organization, or if you have any further questions on the topic.
Thank you for reading, and happy network designing!
Connect with me!
Twitter Account: https://www.twitter.com/sharsha315
LinkedIn Account: https://www.linkedin.com/in/sharsha315
GitHub Account: https://www.github.com/sharsha315